Services
A specialist in the design of secure computing and information management, BSTTech Consulting (BSTTech) is able to advise and provide systems architectures to secure critical information. BSTTech has extensive experience in the creation of highly secure computing systems which meet or exceed Australian Government standards for the management of classified and secure information. This includes extensive experience with building to ACSI 33 standards for the handling of information in these secure environments.This is ideal for Government Agencies, Departments and industries requiring IT systems classification under the Critical Infrastructure Protection Act (including Utilities, Transport, Financial Services and Medical). BSTTech has designed systems for Defence and other government agencies.
Computer Security
System Accreditation |
Identity Management |
Multi-Level Security |
How can your security be improved? Has there been a problem? System Accreditation provides a report on whow your security can be improved. |
Identity Management. The application of a strong management framework for the assignment of physical identities to electronic systems. Policy and Practical implementation. |
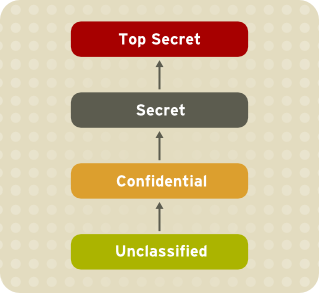
Multi-Level Security The Holy Grail of Computer Security. Access control to information and systems based on business logic and metadata rules, not Groups or Roles. MLS provides the answer. |
System Accreditation and Assessments
A service to look at the current security of your organisation and provide a structured report on how security can be improved. This service relies on interviews and in-depth analysis of your security policy, practices, procedures and processes to provide a business level report on the current state of your security infrastructure. The provision of OS and application hardening services to ensure that exploits and vulnerabilities are mitigated for operating systems (Windows Unix and Linux) and applications such as Databases, HR Systems and eBusiness systems.
Enterprise Architectures and SOA
BSTTech has extensive experience in the scoping, definition, implementation and management of emerging technologies supporting Multi-Level Security. We achieve this through a complete understanding of the systems and information architecture of your enterprise. Mapping this understanding to the current levels of technology within your organisation we can provide a customised and technology agnostic roadmap, based on Enterprise Architecture principals, to allow you to realise your EA dreams.
Identity Management
Are you ready for Identity Management? Can you provide access to your business systems based on roles? Is your infrastructure ready to support true Identity Management? The IM Assessment is for you, it provides you with the roadmap to success for the implementation of logical and physical access control systems! The design, integration and development of identity management systems for adaptive corporate and government IT systems based on X.500, X.509 and biometric authentication systems. The designs provide for:
- A secure identity repository (ies)
- Metadata
- Customisable Workflow
- Authorisation and Certification
- Auditing
- Policy management
- Authentication plug ins
Requirements Management / Definition
In the context of project management, requirements management is the process of eliciting, documenting, analyzing, prioritizing and agreeing on requirements and then controlling change and communicating to relevant stakeholders. It is a continuous process throughout a project. A requirement is a capability to which a project outcome (product or service) must or may conform.
The purpose of requirements management is to assure the organization meets the expectations of its customers, internal or external stakeholders. It focuses on requirements as the element capturing these expectations, and thus as a focal point of the company value chain. It also applies methodologies to include objectives and constraints of the company, in terms of direction and prioritization. Requirements management further includes supporting planning for requirements, integrating requirements and the organization working with them (attributes for requirements), as well as relationships with other information delivering against requirements, and changes for these. The traceabilities thus established are used in managing requirements to report back fulfillment of company and stakeholder interests, in terms of compliance, completeness, coverage and consistency. Traceabilities also support change management as part of requirements management in understanding the impacts of changes through requirements or other related elements (e.g., functional impacts through relations to functional architecture), and facilitating introducing these changes.
BSTTech has experienced consultants to support you in all aspects of the Requirements Management Process
Information Security
Multi-Level Security
Multi-Level Security (MLS) has often been described as the Holy Grail of secure computing. BSTTech has developed, and Patented, an approach to MLS through secure information management which is called MuSE. MuSE uses a number of COTS technology element, working together, to achieve a cross domain information management regime that fully supports the ability to create highly secure Communities of Interest. This is achieved through:
- Strong Identity Management
- Cross platform systems management
- Development of a Digital DNA profile for technology elements and systems
- Information Management
- Super User control
- Device Management
- Information compartmentalisation
- Creation and compulsory application of Meta-data and tags for Identities, systems, information and sessions
- Multiple layers of security and encryption for each session
BSTTech has written a White Paper on the use of this technology which can be found at the BSTTech White Papers section of the website.
Multi-Compartment Systems
Multi-Compartment Security is used where strong seperation of information is required. This can be combined with MLS to provide a superior information management capability . BSTTech has an accredited Multi-Compartment system using a range of COTS technology elements, working together, to achieve a exceptionally strong compartmentisation of information. This is achieved through:
- Strong Identity Management
- Cross platform systems management
- Development of a Digital DNA profile for technology elements and systems
- Information Management
- Super User control
- Device Management
- Information compartmentalisation
- Creation and compulsory application of Meta-data and tags for Identities, systems, information and sessions
- Multiple layers of security and encryption for each session
Technology Options
BSTTech is not focused on any one technology but rather the intelligent use of technology to solve and manage business issues. Through our partners we can leverage multiple technology sets to allow us to provide our clients with the best possible outcomes.